Software & Process Components
The same concept Components is used for the software and process model.
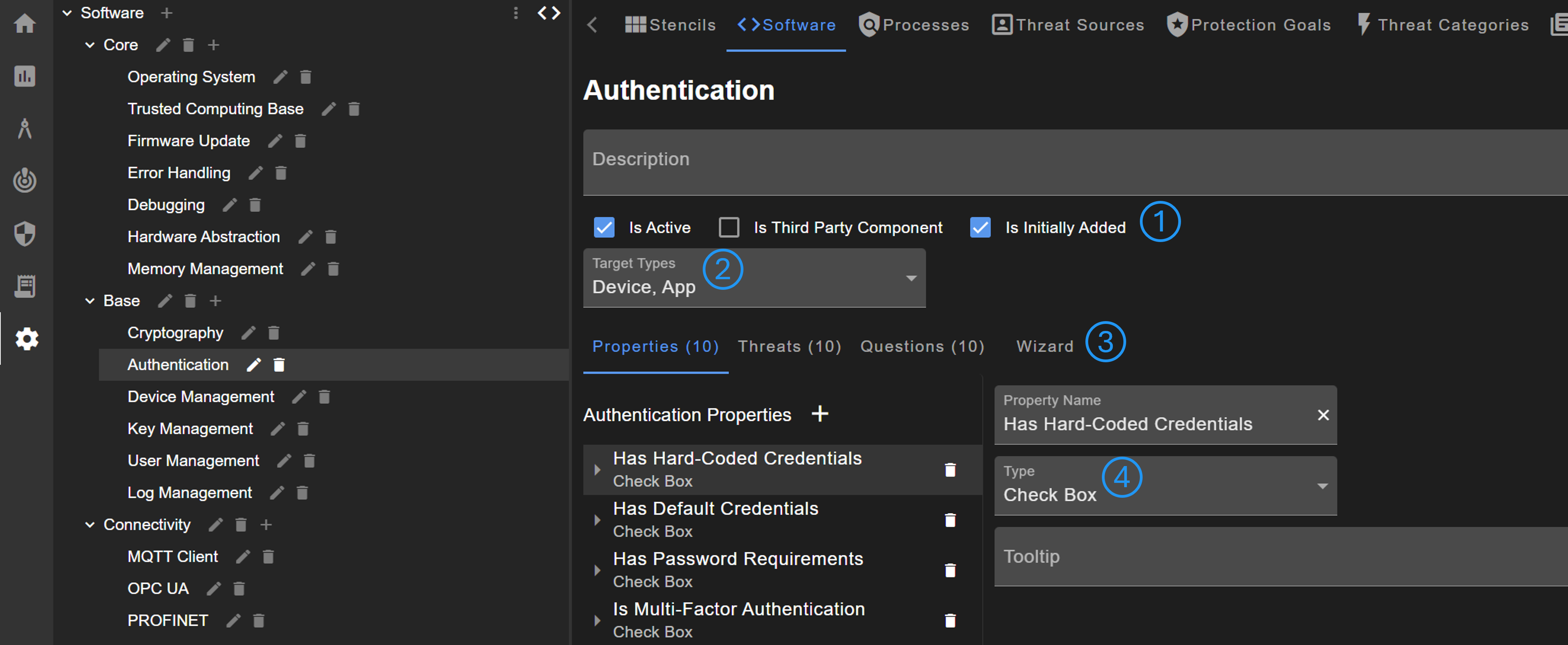
There are a few basic settings for components (No. 1): Is Active defines whether the component is activated, Is Third Party Component can be used to visualize that it is provided by a third party supplier, and Is Initially Added defines whether the component is added to the diagram of a newly created software/process stack.
It is possible to define the target types (No. 2). For example, if the target type is set to device only, the component will not be added to the software model of apps.
The intention of components is as follows:
- Threats to components should be driven by a questionnaire
- Answering a question (currently only yes or no) sets a property to true or false
- Properties can be evaluated by the threat engine and generate threats based on their value
This leads to the following sequence:
- Users answer a question with yes or no
- Configured property gets set to true or false
- Configured threat rule checks whether its restrictions are fulfilled
- An attack scenario is generated
The first three steps need to be configured. This can be done in one step using the wizard (No. 3).
The image above shows exemplary a property. In general, properties can have different types (No. 4). However, at the moment only properties of the type Check Box can be used in threat questions.
Wizard
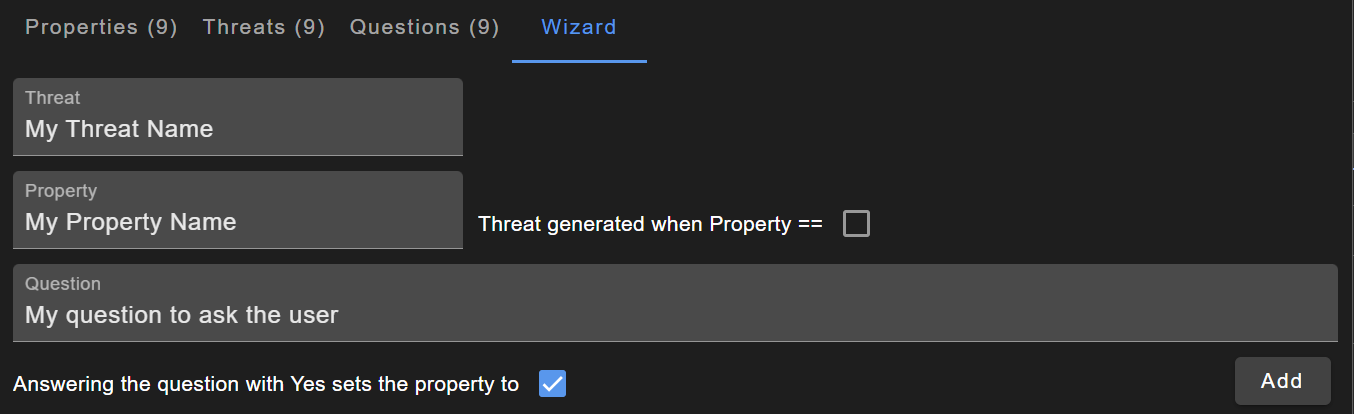
The image below shows the wizard. The fields Threat, Property and Question are self-explanatory. The upper checkbox defines when a threat is generated. An unticked box means when the property is set to false and a ticked box means true. The lower checkbox defines what happens when users click on Yes.
Threat Question
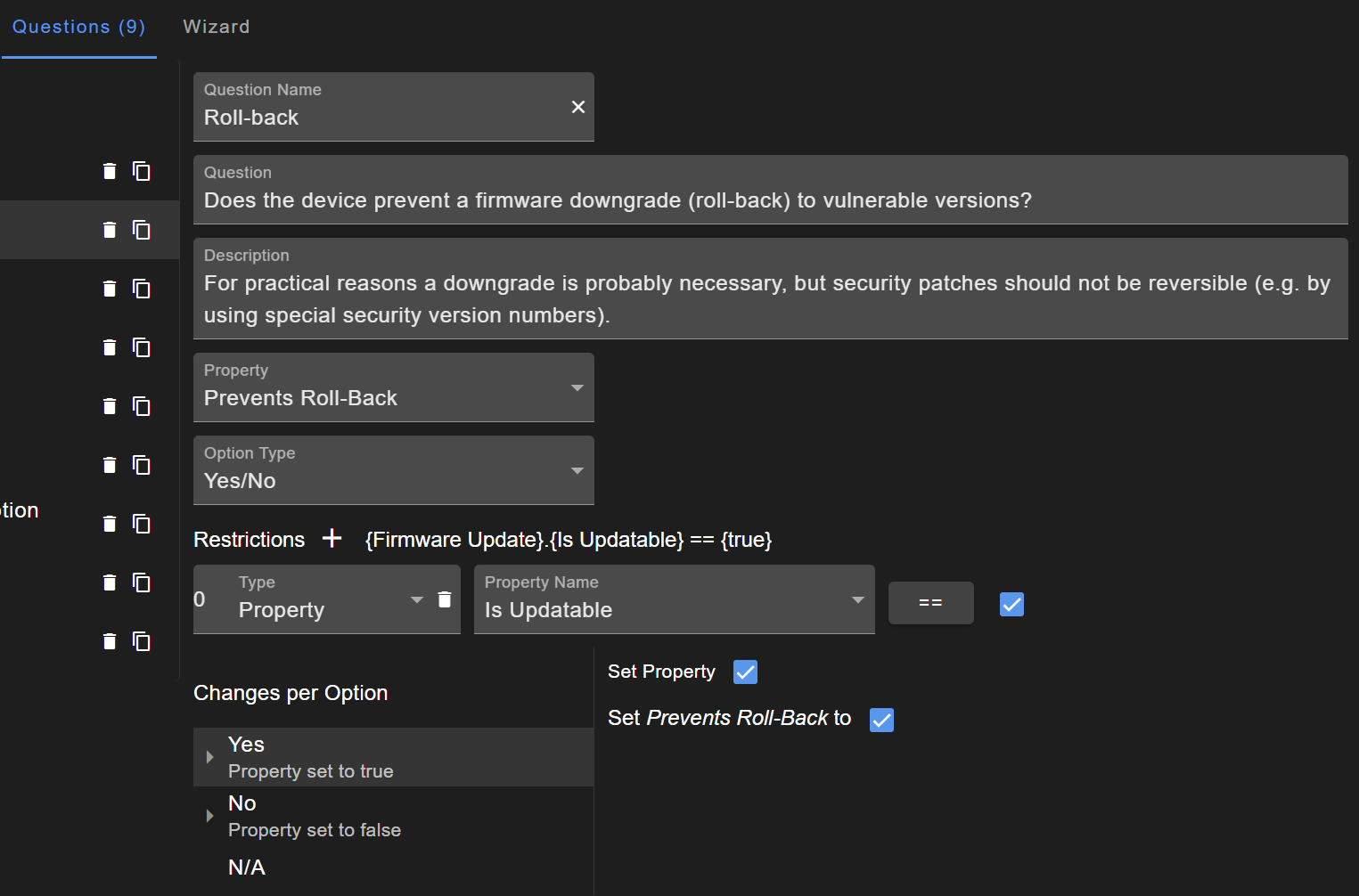
Threat questions are briefly named, provide a precise question, and include a useful description (shown as tooltip in the questionnaire). It needs to be defined which property is associated with the question. This property gets changed depending on the user's answer. It is possible to define restrictions when a question is shown to users. For example, it makes not much sense to ask users whether there is a roll-back protection if an update is not even possible. At the bottom are the changes per option which define what happens when a user selects them.
Threat Rule
The configuration of the threat rule is the same as for stencils and flow diagrams (see Threat Rules).