Risk Assessment
This section describes the configuration of the risk assessment and how to change an assessment method or define a completely new one.
Scales
The tool allows the definition of semi-quantitative scales, which can be assigned to risk metrics. Available scales are listed in the navigation tree as child of Scales, new ones can be added through the '+' button.
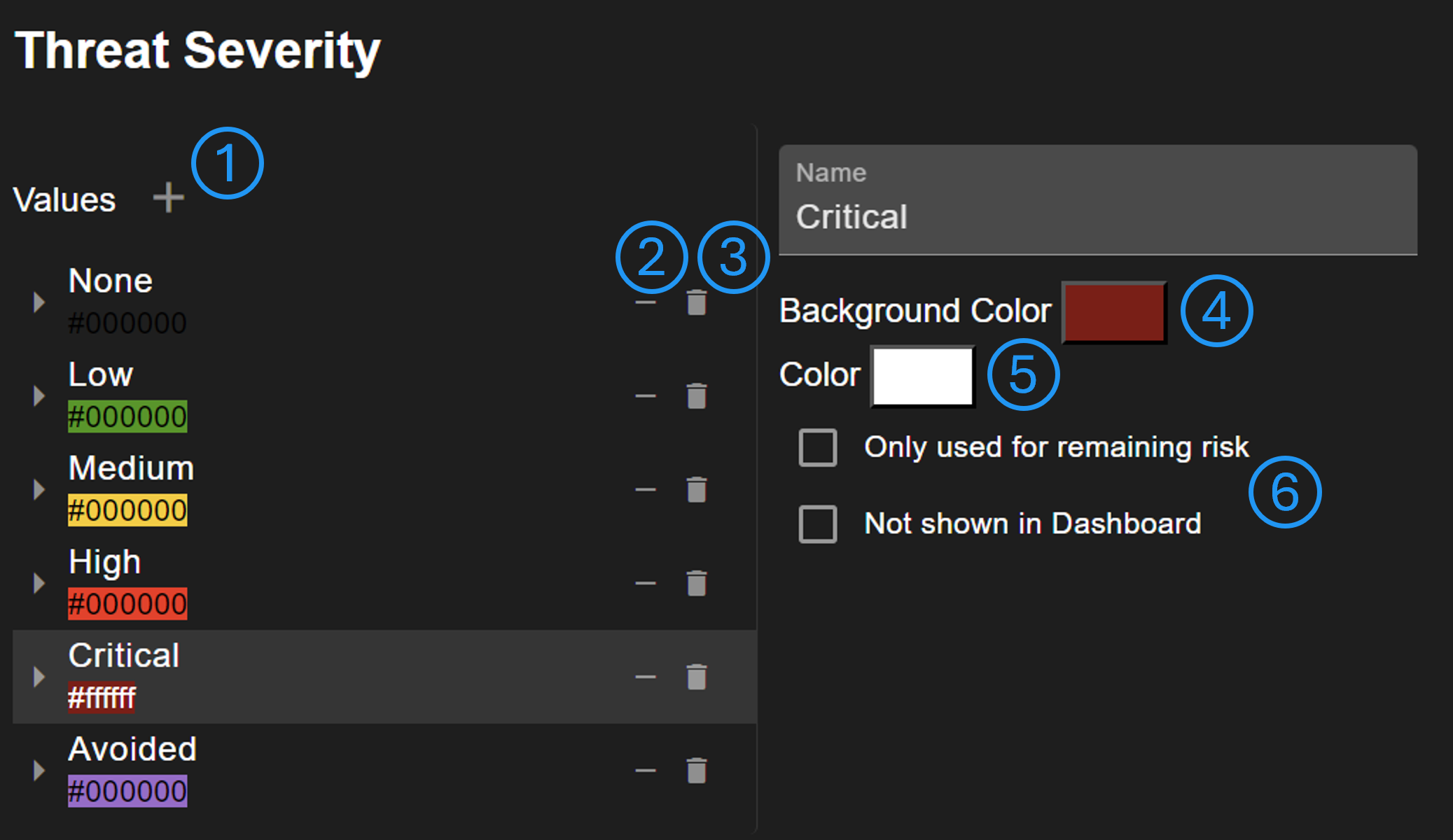
Scale values can be added (No. 1), removed from this scale (No. 2), or entirely deleted (No. 3). It's possible to change the value order by drag & drop. The first item in the list is considered as the least severe and the last as most severe. The order is important, as it is used to generate a mapping matrix, for example. It is possible to change the value background color and the text color (No. 5). It can be defined whether a value is only shown for assessing the remaining risk or whether it is excluded in the dashboard (No. 6).
Risk Assessment Methods
The tool allows the definition of one or more risk assessment methods via the navigation tree. The method is mainly defined by its (sub-)children in the navigation tree. The method itself must have one child, a risk metric, which defines the final risk score. It can be configured which charts are initially created for the dashboard (No. 1). This can be defined for each sub-metric. Furthermore, a risk acceptance level can be defined (No. 2). The risk strategy gets automatically set to 'Accept' if the risk of an attack scenario is equal or less than the accepted level.
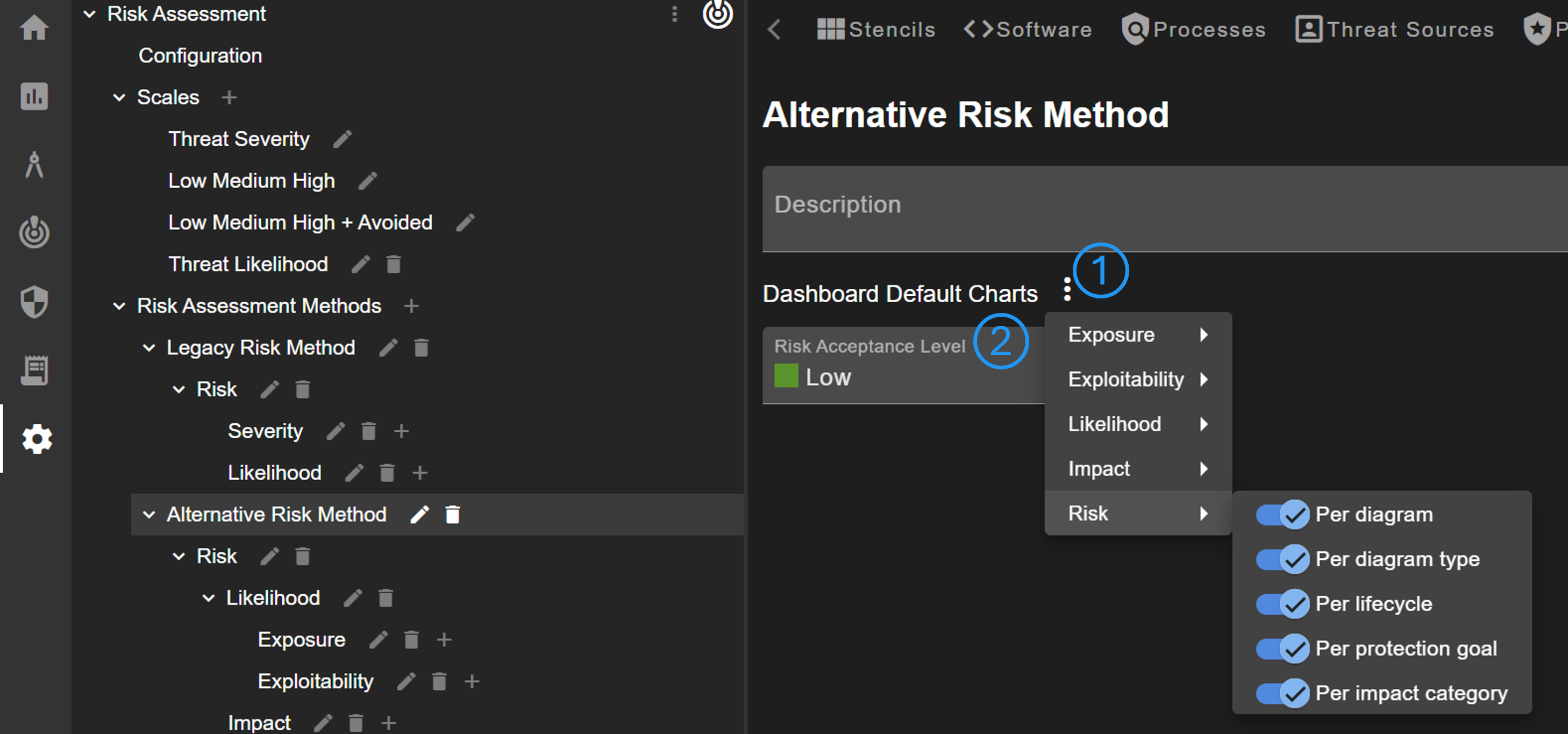
Important
Note that only the default risk assessment method is shown in the dashboard and reporting pages. The default method can be defined in Risk Assessment > Configuration.
Risk Metric
Each risk metric must have a scale, which can be defined or added (No. 1). It can be defined whether the metric is shown to users and whether an attack scenario has notes for the metric (No. 3). Furthermore, setting the metric value can be automated (No. 2). There are multiple automation options, which set the metric value:
- Rule: in case of generated attack scenarios, the severity of threat rule
- CVE severity: the defined severity of a CVE
- CVSS score: the qualitative representation of a CVSS score
- OWASP Risk Rating score: the qualitative representation of OWASP RR score
- OWASP Risk Rating impact score: the OWASP RR impact score
- OWASP Risk Rating likelihood score: the OWASP RR likelihood score
- Maximum impact system threats: the max. impact of all mapped system threats of an attack scenario
- Maximum impact assets: the max. impact of all mapped assets of an attack scenario
- Maximum likelihood threat actor: the max. likelihood of all mapped threat actors of an attack scenario
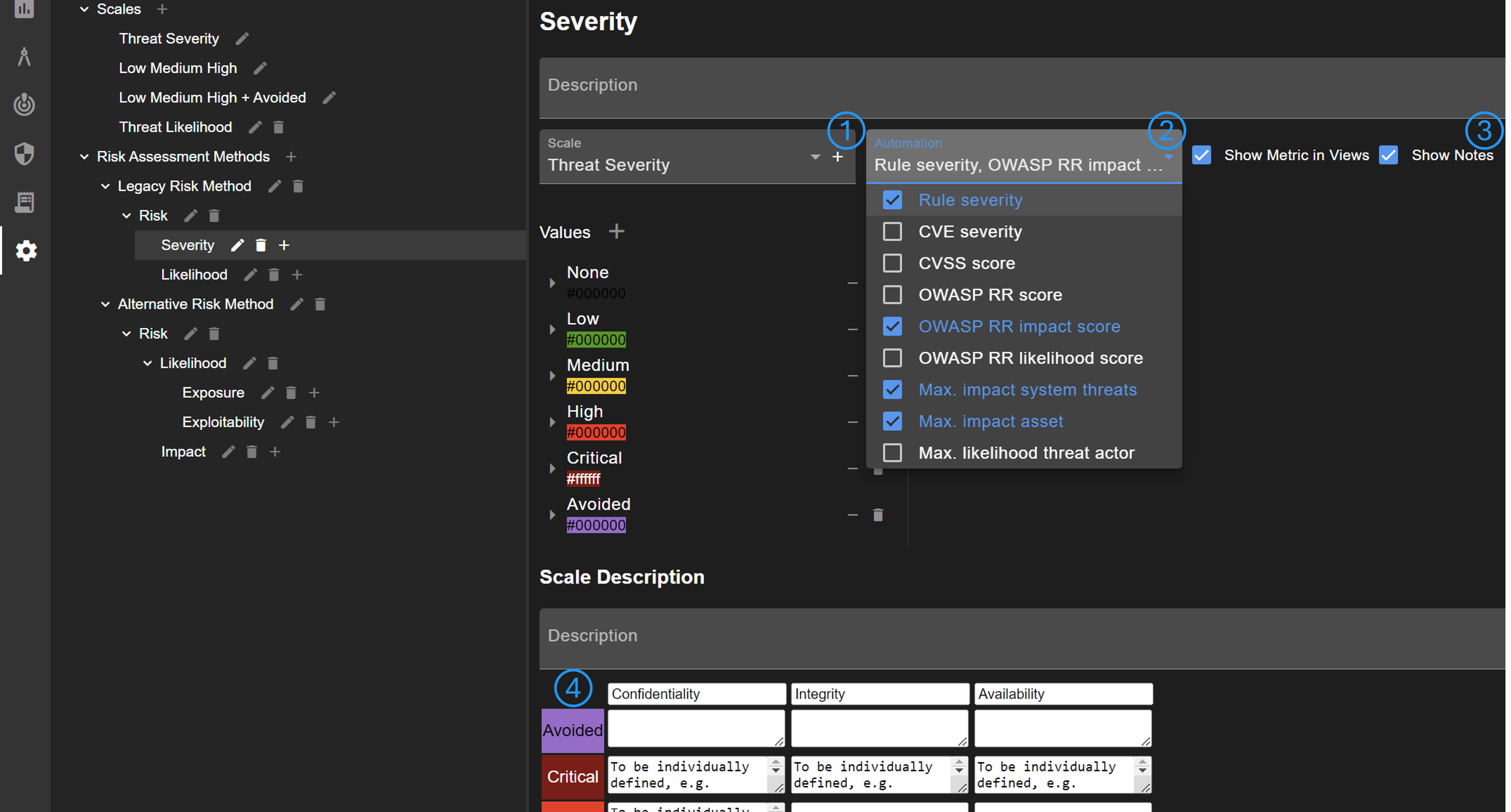
It's possible to provide further explanation for the scale (No. 4). This explanation can be accessed by users via the info button shown in Attack Scenario view (No. 4).
A metric must have either none or at least two sub-metrics. If there are two or more sub-metrics, it must be defined how the parent metric is calculated based on the sub-metrics. Currently, four methods are available.
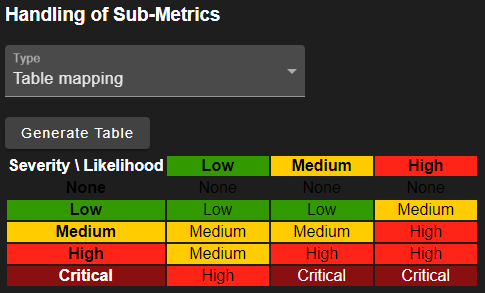
First, a mapping table can be defined, which requires exactly two sub-metrics. The initial mapping can be generated. The values can also be changed by clicking on them.
For the second option, the maximum value of all sub-metrics is used. For this option, the scales must have the same value count.
Another option is to summarize the values of all sub-metrics. This requires that the scale values have the correct value assigned. Furthermore, a range must be defined in order to map the sum to the parent metric.
The fourth option is to define a custom formula. Allowed operators are +, -, *, / and (). Besides numbers, the name of sub-metric can be used. Allowed names are suggested by autocomplete. Again, a range must be defined.

Configuration
There are a few basic settings for the risk assessment, which can be changed under Configuration in the navigation tree. The default risk assessment method can be defined. The selected method is added to new attack scenarios automatically. Note that only the default method is shown in the dashboard, report, and export.
Furthermore, the used scales can be configured. Changing these scales may have an impact on the entire configuration.
Caution
The tool may not work anymore if these scales are configured wrong. For example, changing the rule scale requires to update all configured threat rules. Furthermore, it is not guaranteed that the tool, especially threat generation, still works.
It is possible to change the states for the status of attack scenarios, countermeasures, and mitigation processes. It must be defined for each state whether it "is applicable". States that are applicable are shown as valid items in the corresponding table. Items with a not applicable state are grayed out in the tables and not part of the dashboard or report. Furthermore, the default state for applicable and not applicable must be defined. A not applicable state for mitigation processes is currently not supported.
Change Method of Project
Changing the risk method of an already created project requires some work:
- The shown columns on the Risk page need to be updated
- The shown columns on the Dashboard page need to be updated
- The shown charts on the Dashboard page need to be updated
- If configured, export templates need to be updated on the Reporting page
- Each attack scenario needs to be evaluated again for the new method