Assets
As mentioned in the System Overview, defining assets is an optional but recommended step. Asset-centric threat modelling approaches focus on the individual assets of a system, define their use and criticality, and address why attackers might choose to target this asset and how they could do that. This is not the main aim of this methodology/tool. Nevertheless, these questions are helpful. This step should identify the assets of each actor and classify the sensitivity and impact for each data type.
Goals
The goals of the asset identification are 1) to identify valuable assets in order to better understand the attacker's target and motive/motivation, and 2) to classify the identified data according to their impact.
Defining assets
The tool distinguishes between "general" assets and data, i.e. data is a specialization of an asset. Assets can be anything value, e.g. functions, properties, or intangible things. Data can be files, documents, or information in general.
There are multiple ways to define the assets (No. 1). There is a more visual approach in Asset View and a more structured approach (but equal functionality) in Asset Tree. There is also a separate list just for data. The reference matrix shows which assets are referenced in which diagrams.
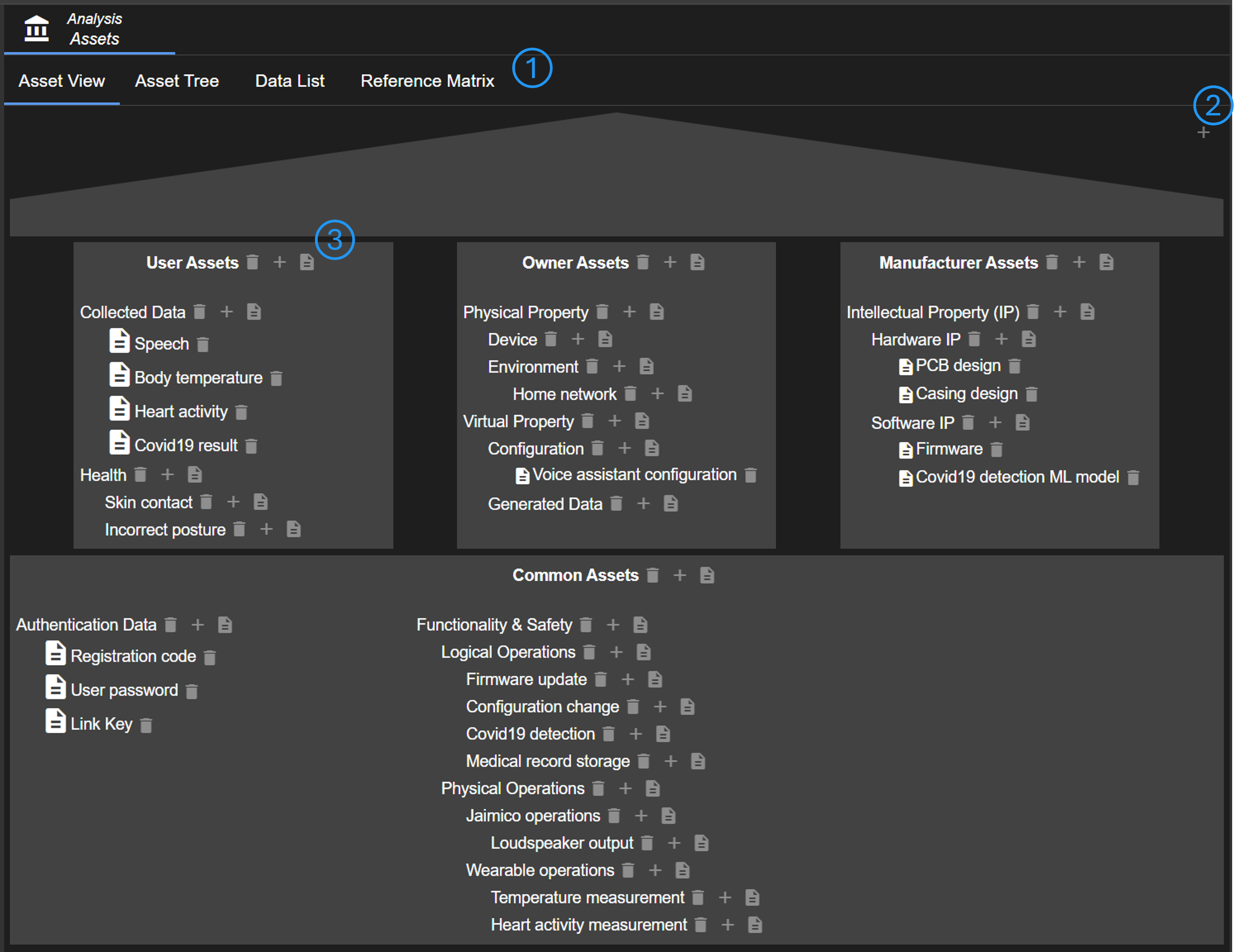
The idea of the shown visualization is that there are common assets for all stakeholders and specific assets for each stakeholder. Putting yourself in the shoes of the various stakeholders can help in the search for assets. The stakeholders may vary in different projects. For example, in some applications there is also a integrator/OEM. New stakeholders can be added via the plus button on the top right (No. 2).
Via the three buttons of each asset (group) (No. 3), the asset can be deleted, a sub-group added, or data added.
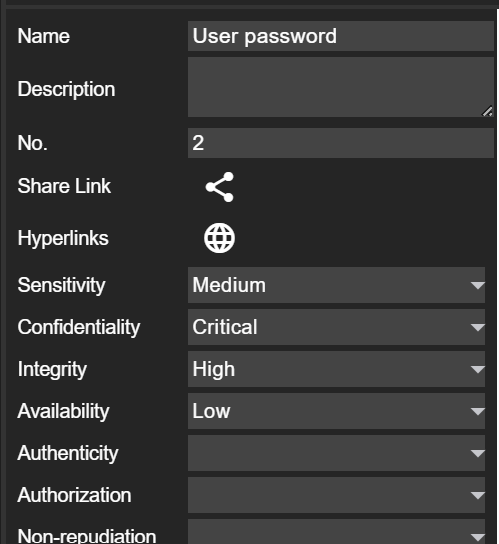
All assets (including data) created by the user have a number assigned that can be referenced in attack scenarios, for example. As some assets are pre-configured, they have no number. If you still want to reference these assets, a number can be assigned via properties.
Global assets and system assets
It is possible to define one global list of assets via Project > Analysis > Assets. In more complex projects, it may be required to define it more fine-grain. Further asset diagrams can be added to each device or app via the add button  .
.