Risk Assessment
It is possible to assess the risk as well as the remaining risk of an attack scenario. For the sake of simplicity, only the assessment of the risk is referred to, although (almost) all points also apply to the remaining risk.
Assessment
The risk can be assessed in different views:
- Attack Scenario
- Risk
- Dashboard
The Risk and Dashboard views contain only dropdowns for the risk metrics. To use all available assessment features, the Attack Scenario view must be used.
Attack Scenario View
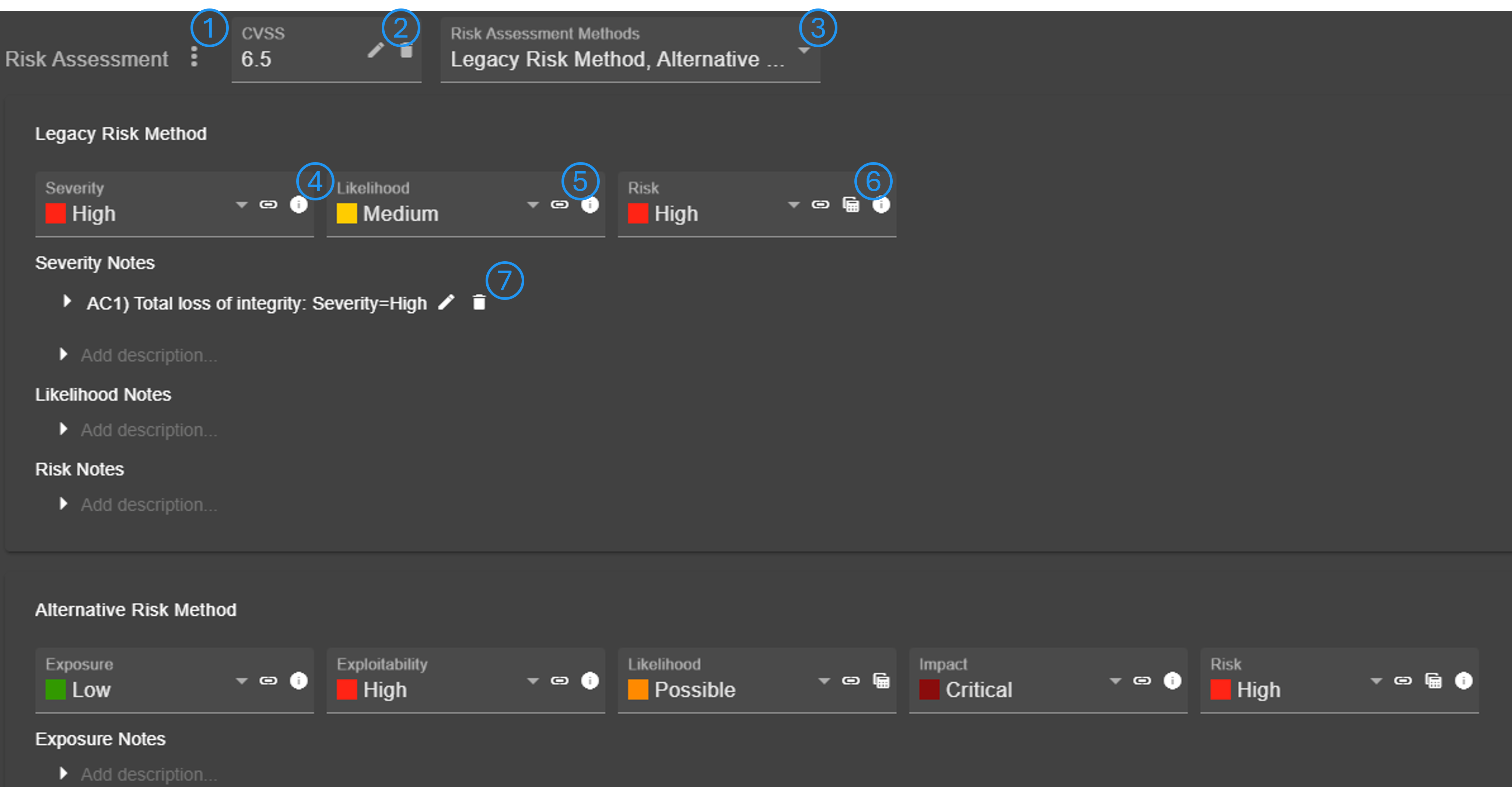
The menu (No. 1) can be used to optionally add an CVSS or OWASP Risk Rating score. Furthermore, the risk rating assessment can be adapted from another attack scenario (which also links both attack scenarios). Scores can be edited in a separate dialog (No. 2). It is possible to assess the risk using multiple risk assessment methods (No. 3).
Each metric of a method is shown as individual dropdown. There may be additional information and explanation available for a metric (No. 4). It is possible to link a predefined assumption/constraint (No. 5) (see Assumptions & Constraints). If a metric is determined using two sub-metrics, a matrix can be opened to view and edit the metric (No. 6).
It is possible to add/edit/delete notes for each metric (No. 7).
Info
Notes may be added automatically, if a metric value is set automatically by code.
Configuration
This section describes the configuration of the risk assessment and how to change an assessment method or define a completely new one.
To configure the risk assessment, go to configuration via the side navigation bar and then open the tab 'Risk Assessment'.
Scales
The tool allows the definition of semi-quantitative scales, which can be assigned to risk metrics. Available scales are listed in the navigation tree as child of 'Scales', new ones can be added through the '+' button.
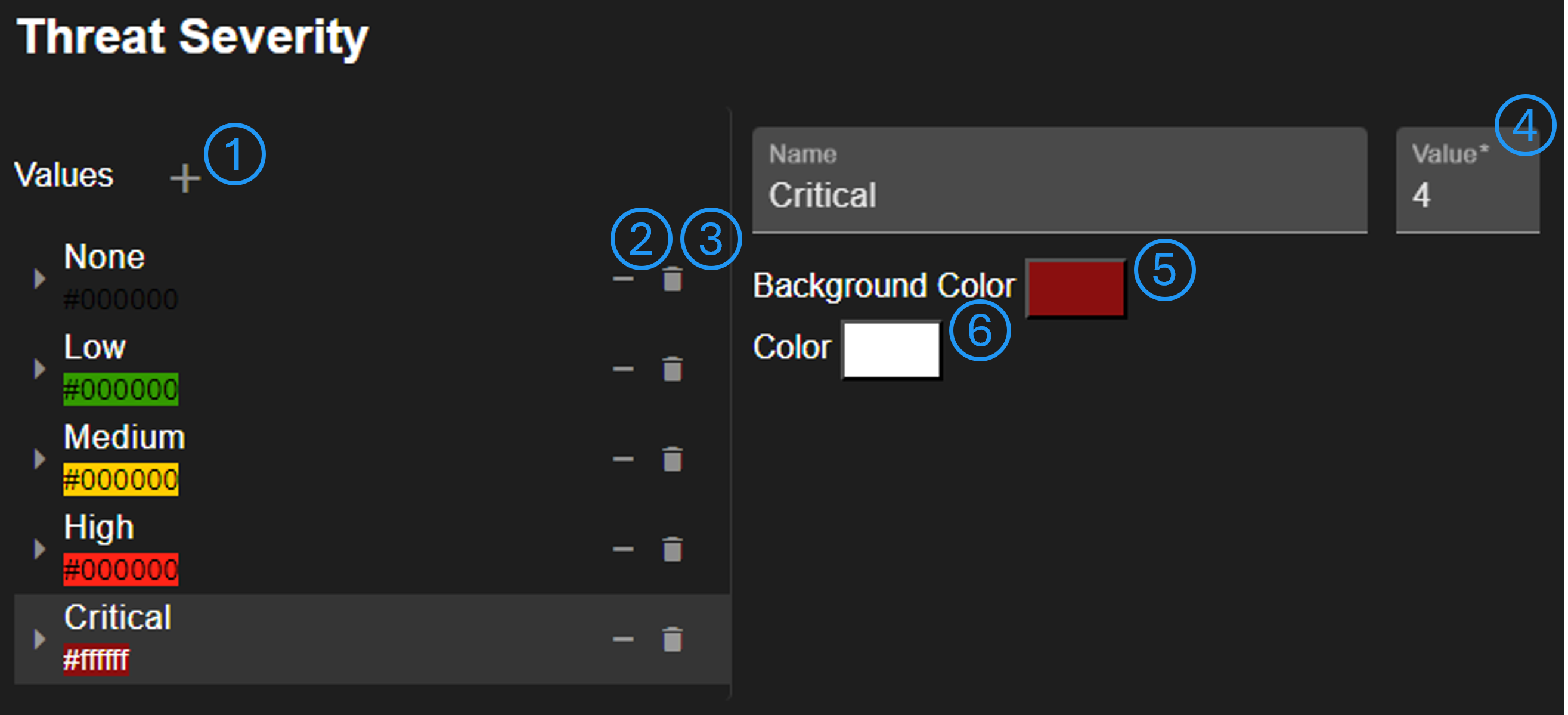
Scale values can be added (No. 1), removed from this scale (No. 2), or entirely deleted (No. 3). It's possible to change the value order by drag & drop. Changing the order does not affect the set value (No. 4), which is used to generate a mapping matrix, for example. It is possible to change the value background color (No. 5) and the text color (No. 6).
Risk Assessment Methods
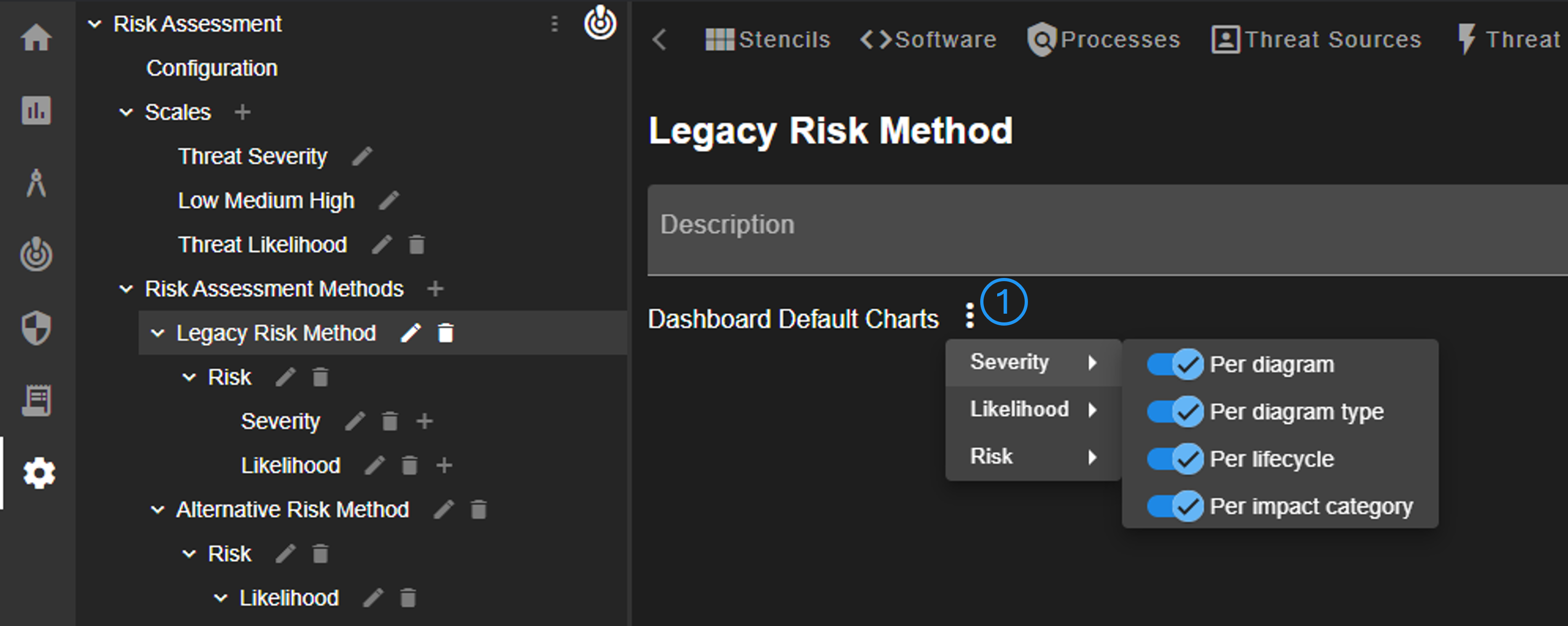
The tool allows the definition of one or more risk assessment methods via the navigation tree. The method is mainly defined by its (sub-)children in the navigation tree. The method itself must have one child, a risk metric, which defines the final risk score. The only changeable property of a method is the configuration of default charts shown in the dashboard (No. 1). For each sub-metric of the method, it can be configured which charts are shown by default.
Risk Metric
Each risk metric must have a scale, which can be defined or added (No. 1). It can be defined whether an attack scenario has notes for the metric (No. 3). Furthermore, setting the metric value can be automated (No. 2). There are multiple automation options, which set the metric value:
- Rule: in case of generated attack scenarios, the severity of threat rule
- CVE severity: the defined severity of a CVE
- CVSS score: the qualitative representation of a CVSS score
- OWASP Risk Rating score: the qualitative representation of OWASP RR score
- OWASP Risk Rating impact score: the OWASP RR impact score
- OWASP Risk Rating likelihood score: the OWASP RR likelihood score
- Maximum impact system threats: the max. impact of all mapped system threats of an attack scenario
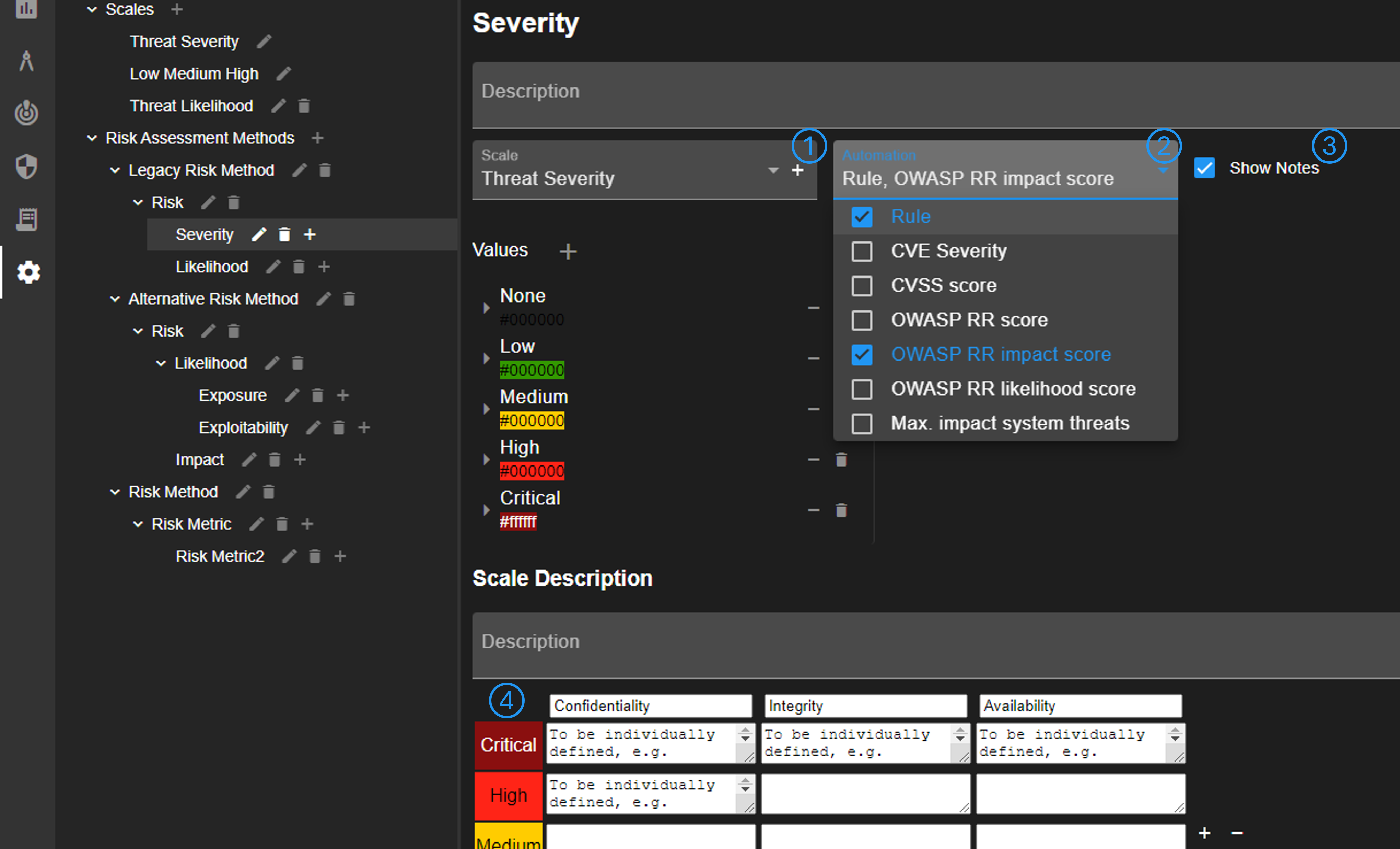
It's possible to provide further explanation for the scale (No. 4). This explanation can be accessed by users via the info button shown in Attack Scenario view (No. 4).
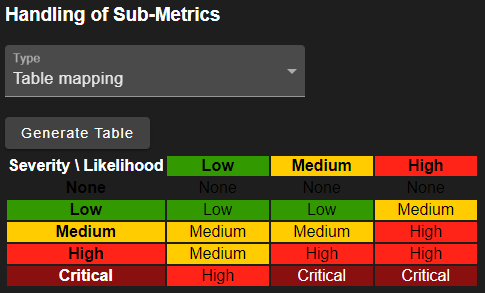
A metric must have either two sub-metrics or none. In case of two sub-metrics, there are two options: 1) Define a mapping table and 2) use the maximum value. In case of the table, the initial mapping can be generated. The values can also be changed by clicking on them. For the second option, the maximum value of all sub-metrics is used. For this option, the scales must have the same value count.
Risk Assessment Configuration
There are a few basic settings for the risk assessment, which can be changed under 'Configuration' in the navigation tree. First, the default risk assessment method can be defined. The selected method is added to new attack scenarios automatically. Second, the used scales can be configured. Changing these scales may have an impact on the entire configuration.
Warning
The tool may not work anymore if these scales are configured wrong. For example, changing the rule scale requires to update all configured threat rules. Furthermore, it is not guaranteed that the tool, especially threat generation, still works.
Assumptions & Constraints
Assumptions & Constraints (ACs) can be pre-configured in a separate tab 'Assumptions & Constraints'. These ACs are useful to assure consistent risk assessment.
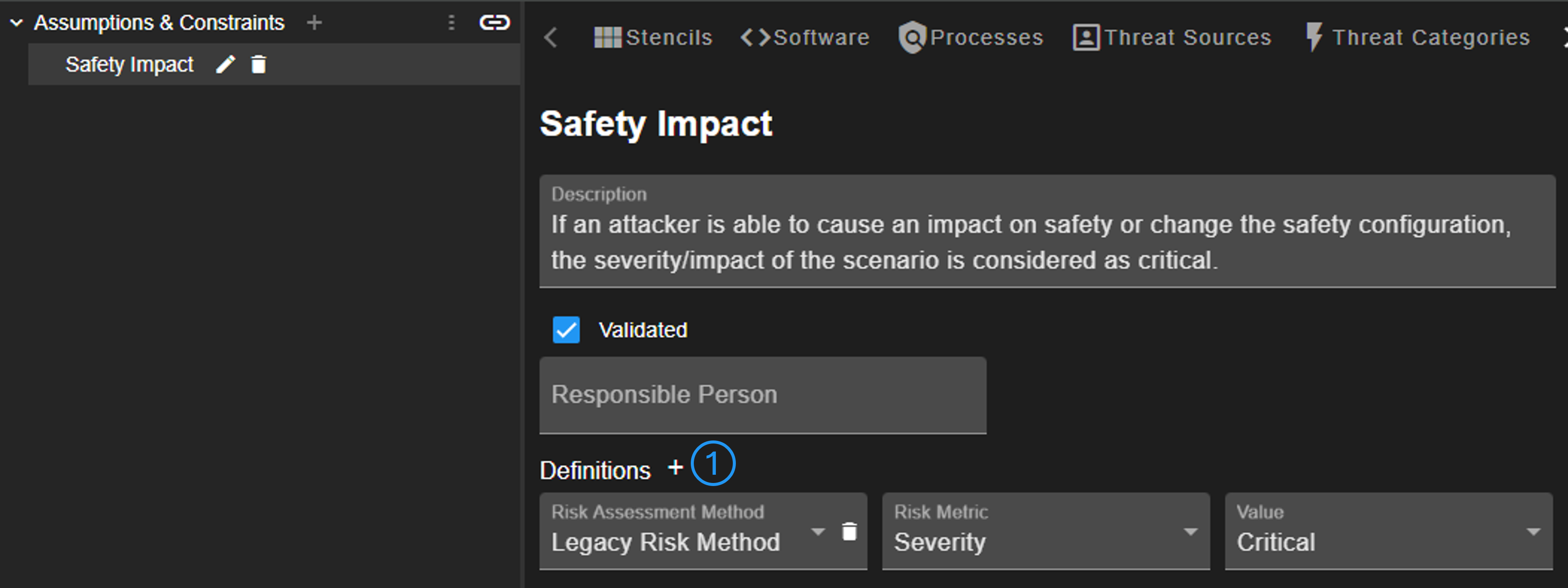
ACs enable the creation of definitions (No. 1), which are used for automating risk assessment. Multiple definitions can be added that set the configured value, if linked to an attack scenario.
The pre-configured ACs are added to a new project on creation. Linking the project-ACs can be done via the chain button shown in Attack Scenario view (No. 5).